TRAVIS WEATHERS
Optiv Security
BOLO
Ralph May

Black Hills Information Security

AGENDA
H0w? Are You For Real?
How? Evasive facility breach in 15-minutes or less
CAVEATS
- Properly scoped with clearly defined intent & goals
- Goal #1 = Always Physical Access
- Goal #2 = Whatever keeps your client (CEO, Stakeholders, CLO/General Counsel) up at night
- Goal 3+ = May increase time on target
- Solid Operating Methodology (that is followed to the T)
- Go in with the mindset of "Once your cover is blown, the engagement is over"
- Don't be a hero and stick to the plan!

How? Evasive facility breach in 15-minutes or less Cont.
- Good Remote Recon reduces the need for On-site Surveillance
- Properly executed Threat Profiling ensures effective Facility Exploitation
- Well understood Client Intent and LoA increases success
- Solid Action Logging reduces conflict and CSAT/Legal issues
All of the above are the perfect ingredients for a smooth, effective, and impact Facility Breach

Got it... But How?
- It takes longer than 15-minutes...
- Remote Recon
- On-site Surveillance
- Threat Profiling
- It only takes 15-minutes (in most scenarios)
- Facility Access (Exploitation) - Goal #1
- Post-Exploitation - Goal #2
Let's dive into the weeds a bit...

Remote Recon
Things to look for:
- Workplace dress code
- Nearby lunch/break venues
- Operating hours
- Badge design (orientation, logos, photos)
- Helpful websites:
- Google (Maps, Images, Web)
Remote Recon – Digital Analysis


Search the following:
- Company name
- Address
- Hashtags
- Tagged section
- Analyze who follows / comments / shares posts
Remote Recon – instagram

Remote Recon – Linkedin

Search the following:
- Job Postings
- Technologies Used
- Employee names / titles
- Company events
Leverage this information to assist in an SE scenario or to talk your way out of getting caught.

| ACTION | ACTIONS | NOTES |
|---|---|---|
| Arial Map Analysis | - Determine the general layout of the facility/campus. - Determine employee density through analysis of the parking lot/structure size. - Identify nearby establishments that employees may frequent. - Traffic patterns in and out of the area |
Use various mapping sources (.e.g, ArcGIS, Bing, Google Maps/Earth, etc.) |
| Street View Map Analysis | - Identify camera placement & viewing angles. - Chokepoints that can be leveraged for badge cloning - Areas that might be best situated for in-person surveillance - Parking and facility ingress/egress points |
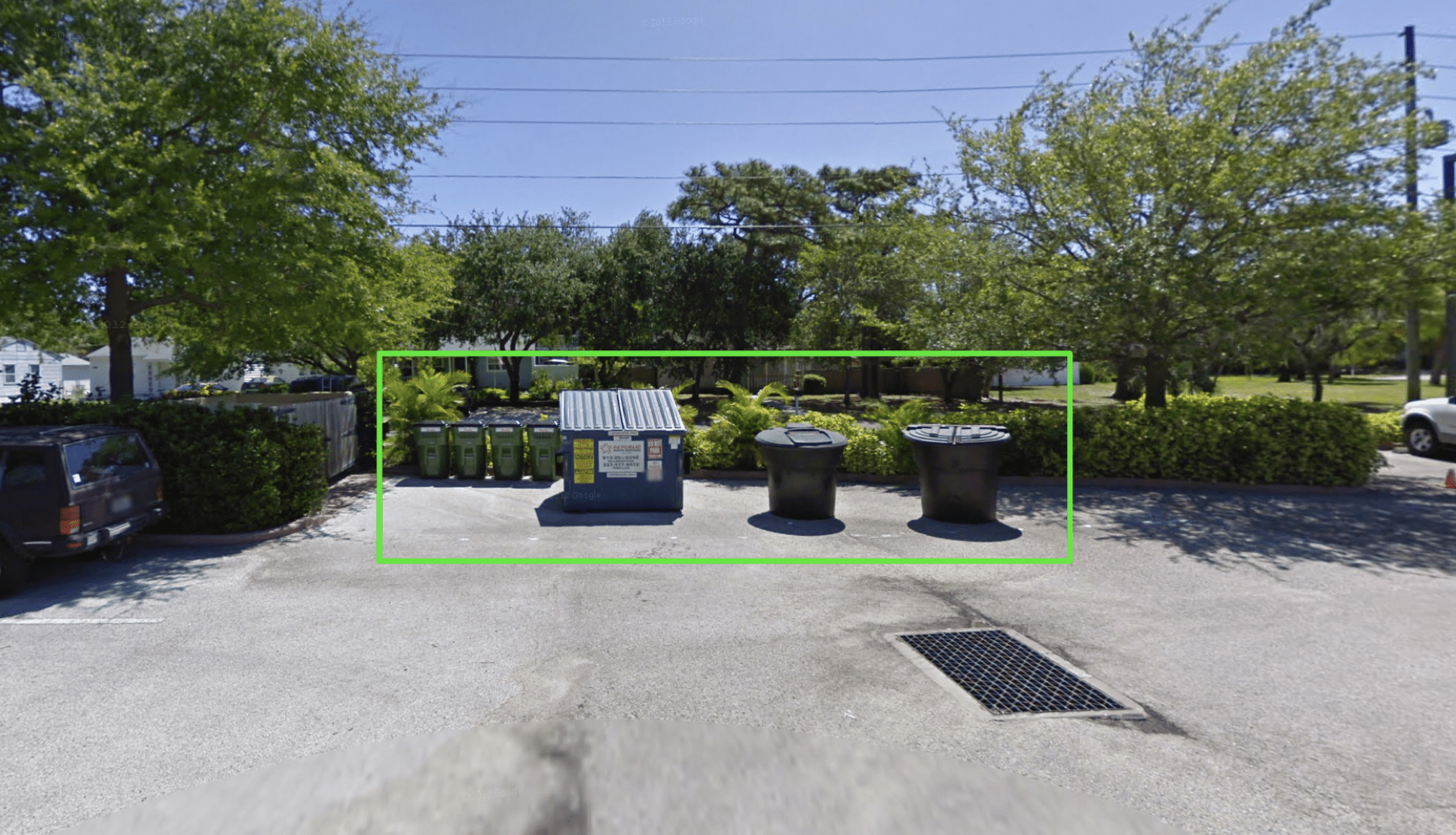
Can you determine the location of trash recipticals or security staging locations? |
REMOTE RECON - GEOSPATIAL RECONNAISSANCE

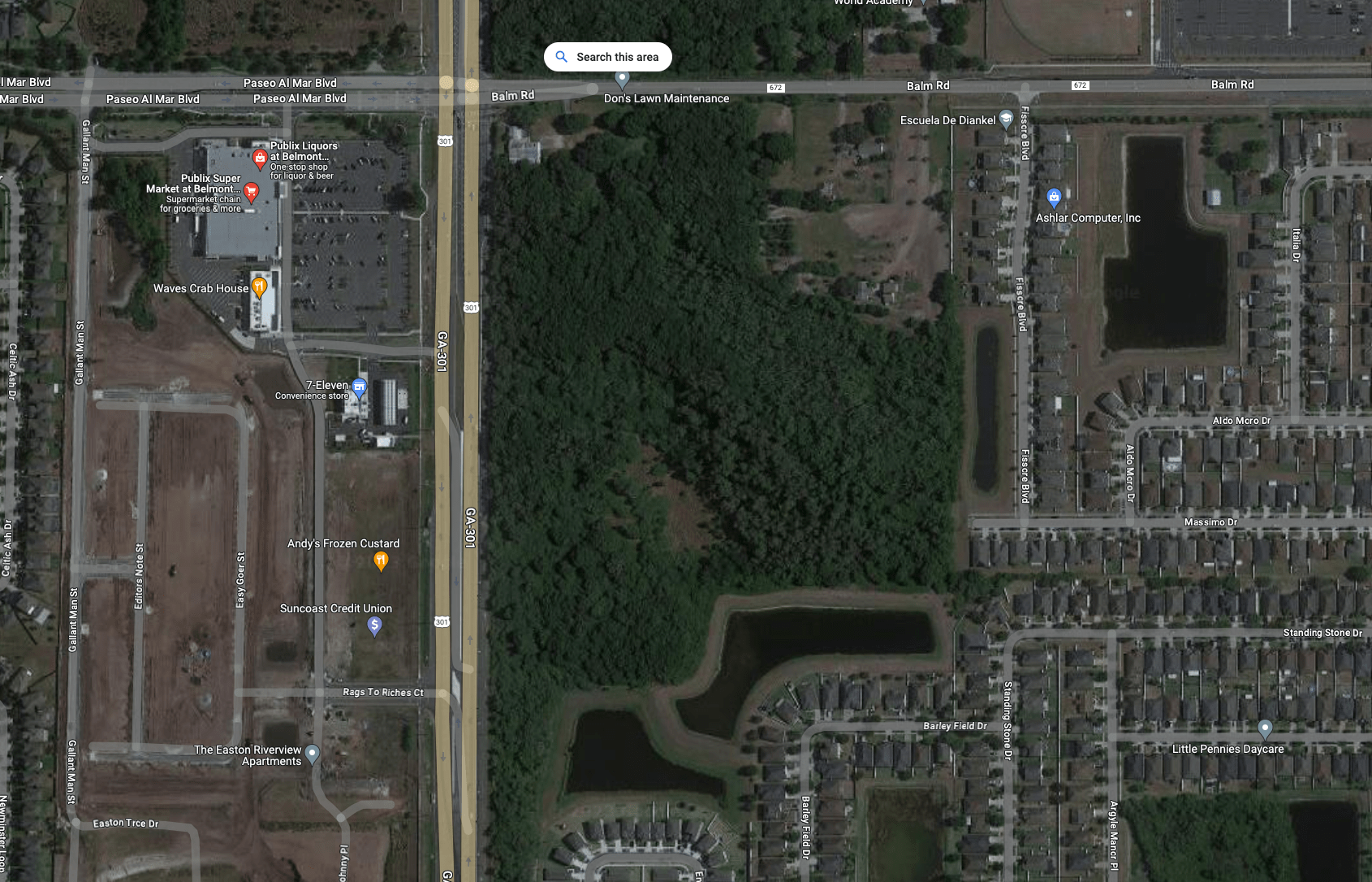
Google Maps

remote recon - GeospatiaL REcon
Bing Maps
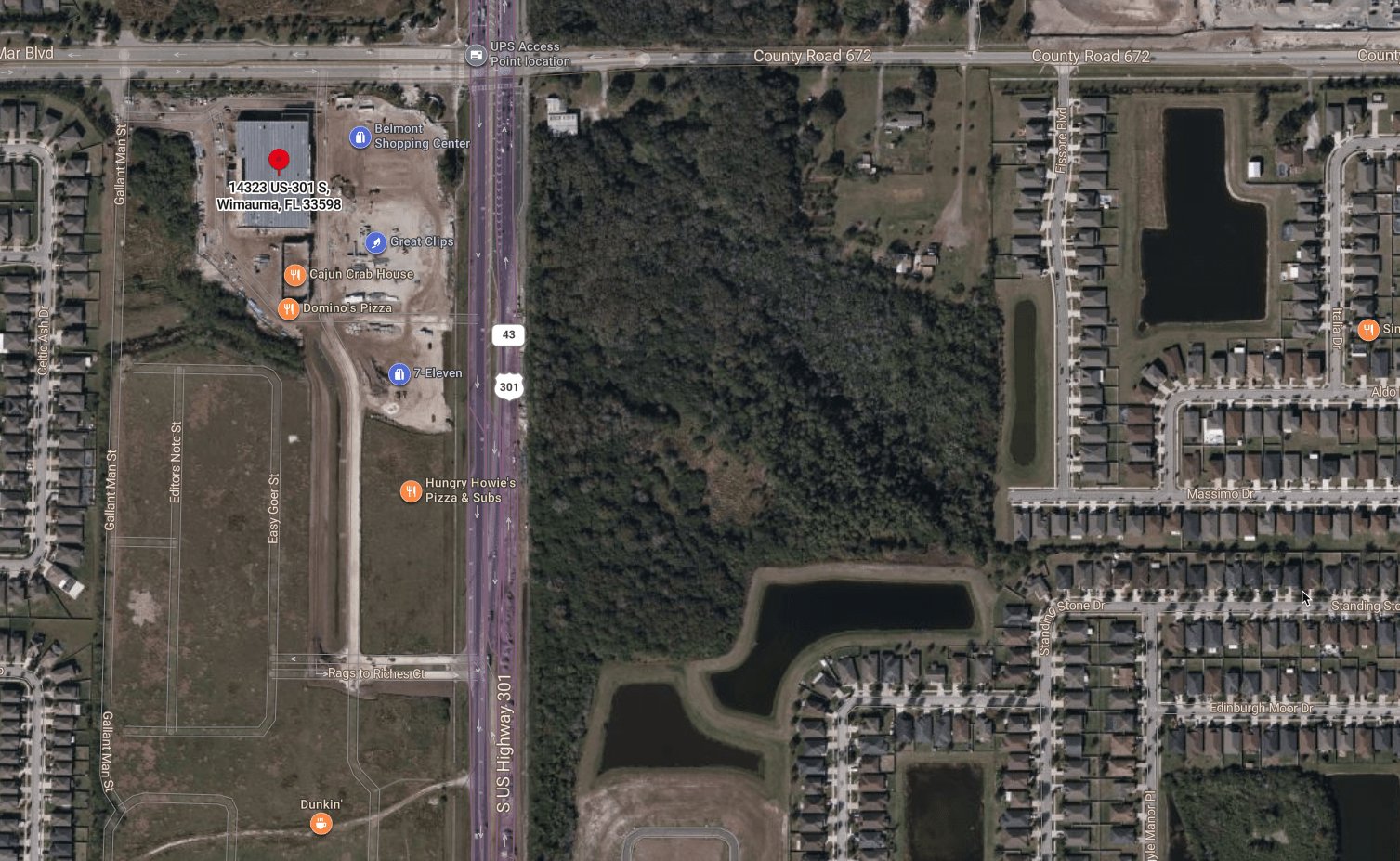
ArcGIS
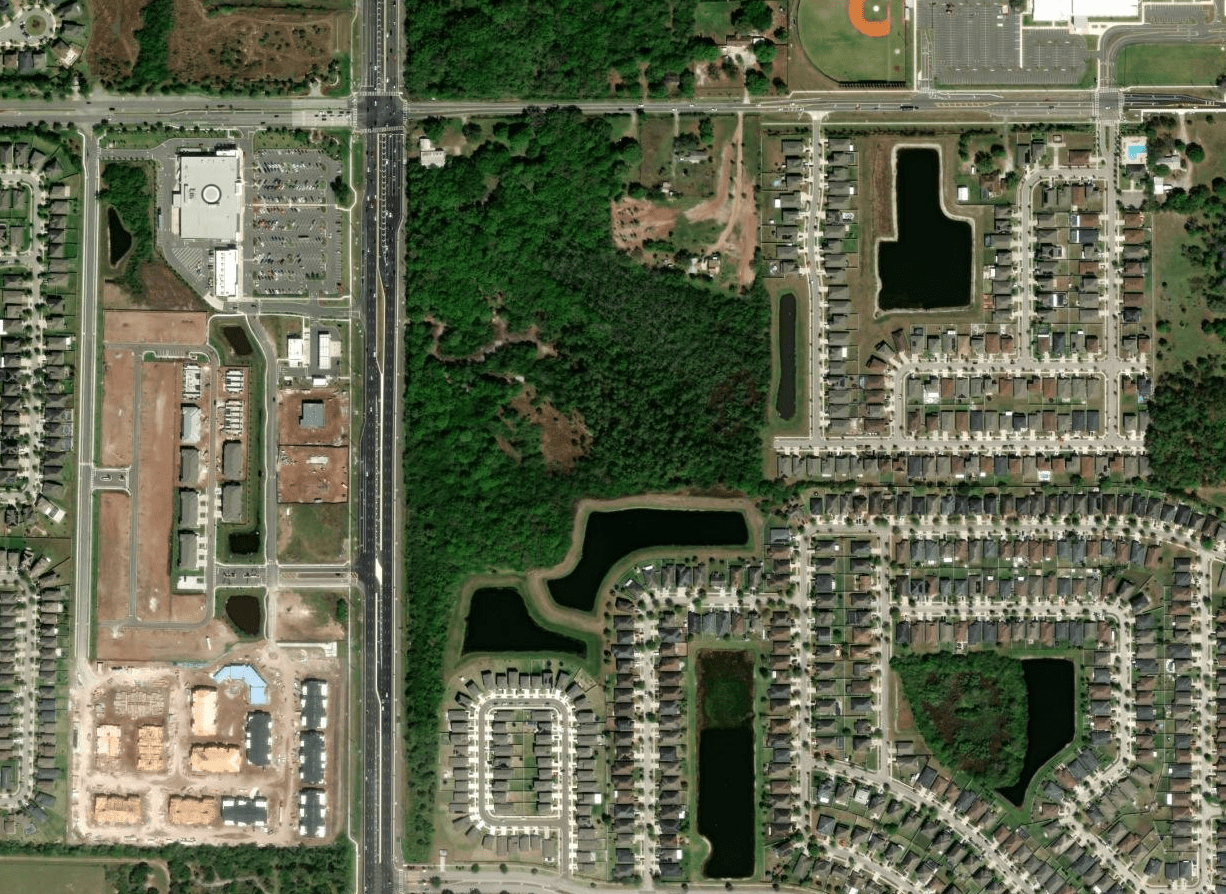
Attack Path Planning
- Ingress/Egress Points
- Potential chokepoints (for badge cloning)
- Structure floor plan
- Trash receptacle placement?
remote recon - Street View



On-Site Surveillance Staging
- Figure out where you want to be for on-site surveillance
- Note areas of no/insufficient coverage
- Note areas where you want to avoid
on-site Surveillance

Considerations
- You're on-site, and everything you do can compromise the engagement
- Do NOT expose yourself more than needed!
- If you have what you need from Remote Recon, confirm and move on
- This isn't a stakeout; get what you need and get out
- Sound, light, movement & reflection awareness
- Don't be a hero, stick to the plan!
- If it sounds like a questionable decision in your head, it probably is

MOBILE recon – Types
Mobile Recon Types
- Dynamic Analysis - Vehicle in motion
- Static Analysis - Vehicle is stationary (*optional/only if required)

MOBILE recon - Dynamic Analysis
Tooling
- Mobile Phone / GoPro / Dashcam
Body Posture
- Don't be a lookie-loo
- Let your tooling do the work
- No more than two passes, ideally more than 20 minutes apart
- Use your Remote Recon output to determine your route
- Only having the tooling required to accomplish the job

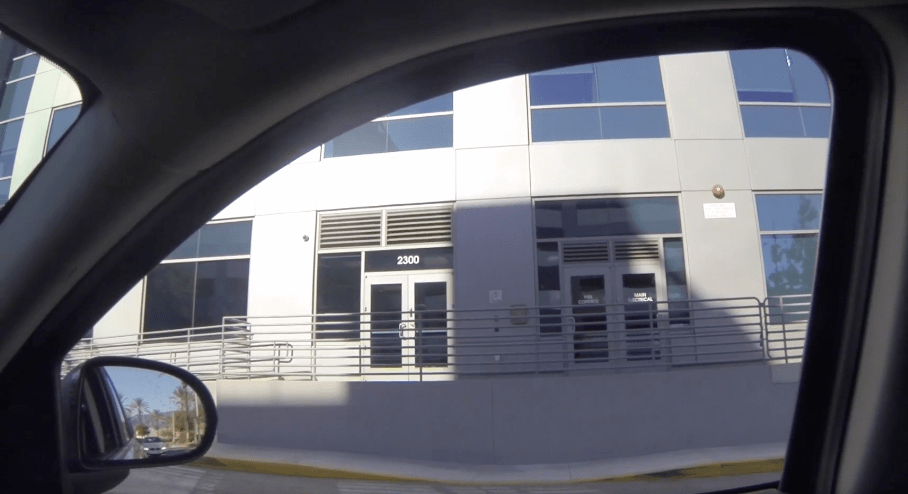

MOBILE recon - Static Analysis
Tooling
- Telephoto Capable Camera
- Something to take notes
Considerations
- Don’t get closer than necessary!
- Use adjacent parking lots/businesses if possible
MOBILE recon - Static Analysis

Employees
- Badge exposure policy?
- Operating Hours
- What is the general business attire?
- Does it look like employees tailgate each other?
Guards / Service Providers
- Guard Desk / Receptionist Location
- Guard Shift Change Times
- Armed / LEO?
- Roaming Guard Presence & Frequency
- Shifts?
Security Cameras / Controls
- Placement, viewing angles, coverage area and types?
- Request to Exit (REX)
- Push to Exit (REX)
- Anti-piggybacking
- Mechanical / Digital (RFID) Locks
- Mantraps / Turnstyles
Reader Protocol (e.g., Prox. EM, iCLASS, multiCLASS)
- Single factor (e.g., just card)
- Multi-factor (e.g., keypad / bio-metric)
Facility
- Chokepoints
- Vehicle/Foot Traffic
MOBILE recon - Static Analysis Cont.
Security Cameras
- Placement, viewing angles, and coverage
- Type:
- Varifocal Lens
- AI
- License plate
- PTZ
Reader Protocol (e.g., Prox. EM, iCLASS, multiCLASS)
- Single factor (e.g., just card)
- Multi-factor (e.g., keypad / bio-metric)
Facility
- Chokepoints
- Vehicle/Foot Traffic
Mechanical Lock Types
- Traditional locks
- High-security locks
- Latch guards
Motion Sensors
- Request to Exit (REX)
- Push to Exit (REX)
- Anti-piggybacking
Floor / Parking Area Access
- Man traps
- Stairwell
- Turnstyles
- Elevators


Close Proximity Surveillance
Tools
- Mental notes
- Mobile phone
Considerations
- Reference Camera Placement / Viewing Angles before approaching
- Blend in w/ employees
- Don’t be obvious when taking photographs
- Dim device screen all the way, on vibrate, disable shutter sound, use ide button shutter, sometimes video is better (extract screenshots later)
- Have an evacuation plan

Threat Profiling

PRIORITIZATION of Attack Paths
Compilation of remote & on-site recon to determine the most likely path to success with the least resistance while remaining within the limits and intent of the engagement.

PRIORITIZATION - Examples
| Attack Scenario | Observations | Effort | Risk |
|---|---|---|---|
| Badge Cloning | - Employees expose badges outside the facility - Facility uses cloneable access card technology - Coffee house directly adjacent to facility |
- Off-site staging is possible - Cloning efforts can occur in line or at multiple chokepoints - Long-range reader required |
- Risk of discovery if too close - Risk of discovery off-site - Chance of RF interference - Chance of capturing third-party access card crendentials |
| Social Engineering | - Building is adequately hardened (e.g., bio-metrics, anti-piggy backing controls, etc.) - XYZ service vendor performing facility repairs - Limited access widow for testing |
- Telephony spoofing for pre-validation (client employee) - Telephony spoofing for pre-validation (XYZ vendor) - Pose as XYZ oversight manager - Create a replica vendor ID card/business card, etc. - Off-site validation |
- Direct exposure to security guard - Only one chance at success - Pre-validation fails - BOLO |
| Surreptitious Entry | - Access to unprotected door on second story balcony | - Use of ladder/rope/grappling hook - Limited to after-hours |
- Roaming guards - Possible view from a wide-angle security camera - Exposure from overhead lighting |
15-Minute Access Window

Access Example
| Engagement Goal | Required Tooling | Timeline | Cover Story |
|---|---|---|---|
| Gain access to the production floor and access intellectual property | - HID Prox reader w/doppelganger for cloning - Proxmark3 for writing card data - Replica ID Card - Method to unlock / shell workstation or drop-device - UDT & Lockpicks? - Authorization Letter |
Complete: Create Replica Badge (found on Insta) 08:00-08:30: Arrive at off-site location for cloning 09:00-11:00: Write cloned card data, validate drop device works, finalize cover story 12:30-12:45: Enter the facility during lunch, identify the production floor location, and plant the device/shell workstation if possible 13:00: Depart facility |
Sent from XYZ department to investigate malfunctioning widget that was generating alerts. |
Badge Cloning
Shameless Plug...

Three Days / Tampa, FL
- Pre-sales & Authorization
- Remote Reconnaissance
- Digital Surveillance
- Surreptitious Entry Tactics
- Badge Cloning & Replication
- Post-Exploitation
- Live Facility Breach Exercise
Upcoming Dates (2024):
May 8 - 10
July 17 - 19
October 16 - 18
PRIVATE TRAINING AVAILABLE
Tooling Available