An Attacker’s Perspective


TRAVIS WEATHERS
Optiv Security
BOLO
Ralph May


AGENDA
how do we attack
What we do
-
Recon
- Remote
- On Site
- Threat Profiling
- Attack the easiest target
- Post Exploitation / Primary Goal
What we don't do
- Drive though the front door
- Hurt people / Active Shooter
- Destroy Property
- Property Theft
attacker mind set
- Goal oriented (securing your facility will require looking at everything)
- Low Hanging Fruit
- Social Engineering
- Get in Get out
- There is a budget not all tech is in the budget
- Not everything is a good value
- Only you can decided what you want to protect
- Human life should be top of the list
warning
recon
Types of Recon
Badge Exposure
Geospatial (Google Maps)
Street View
GRG (Gridded Reference Graphic)

badge Recon Remote


Search the following:
- Company name
- Address
- Hashtags
- Tagged section
- Analyze who follows / comments / shares posts
badge Recon ONSITE


Go Looking for Badges:
- Go to local lunch spots
- Watch as people leave the faculty
- Do recon no need to confront people
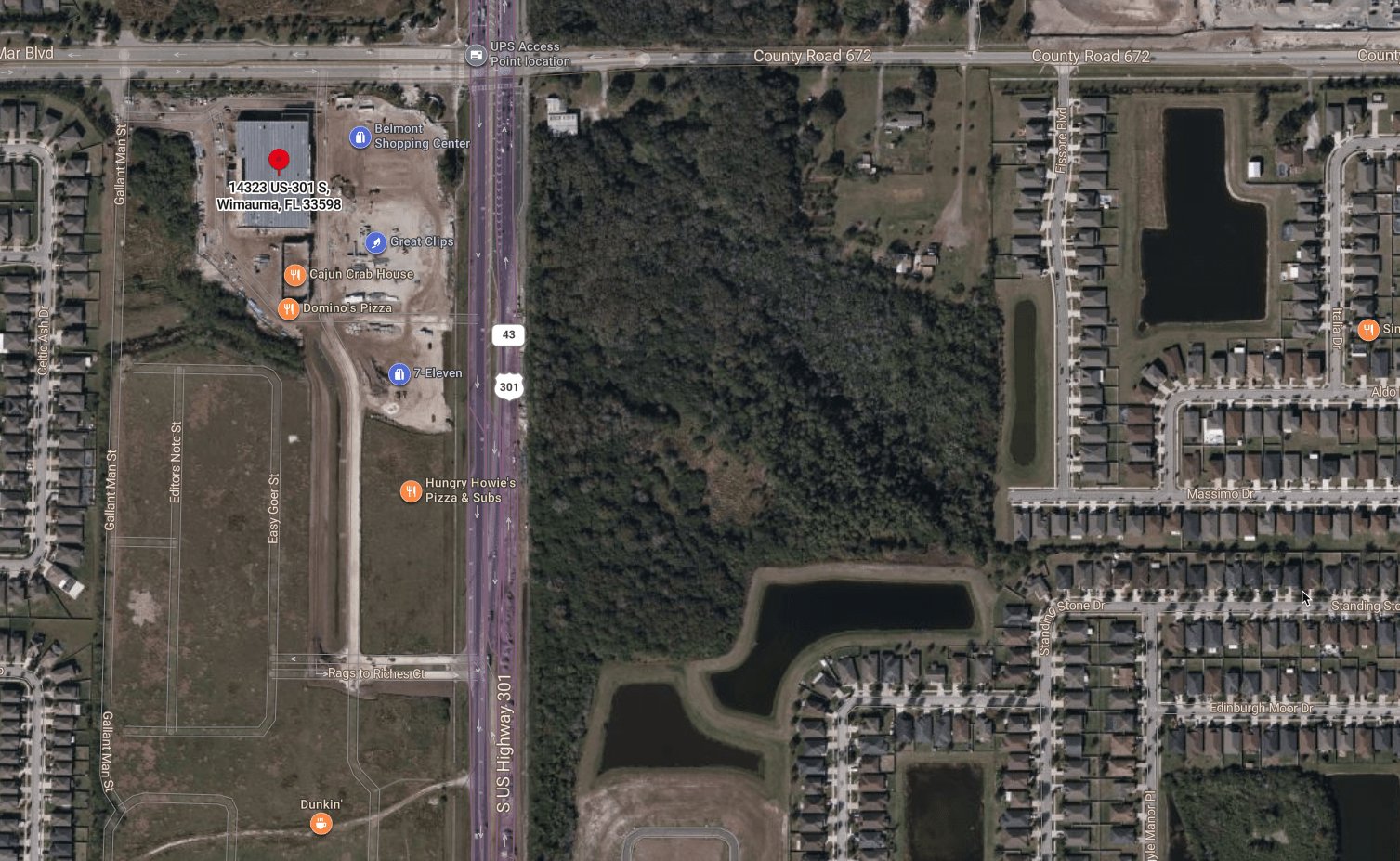
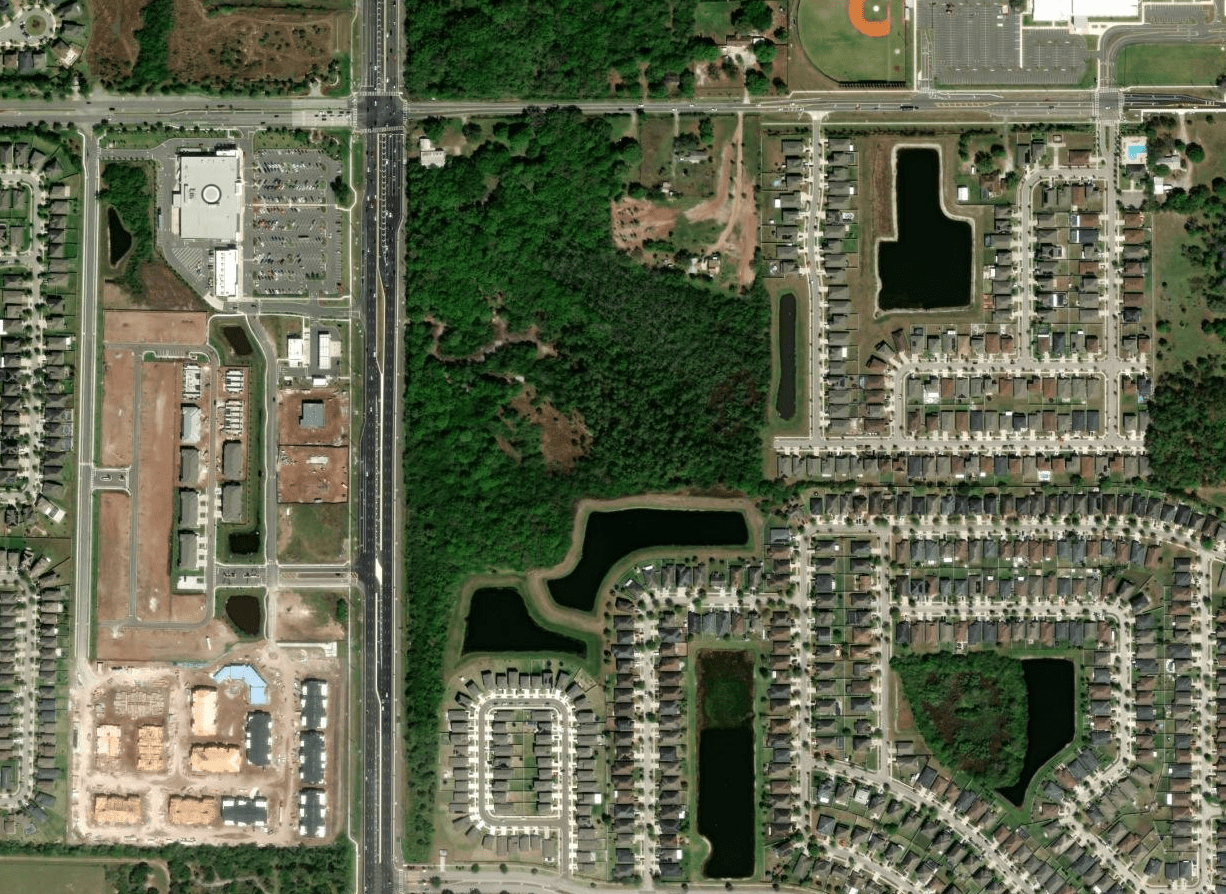
GEOSPATIAL RECON

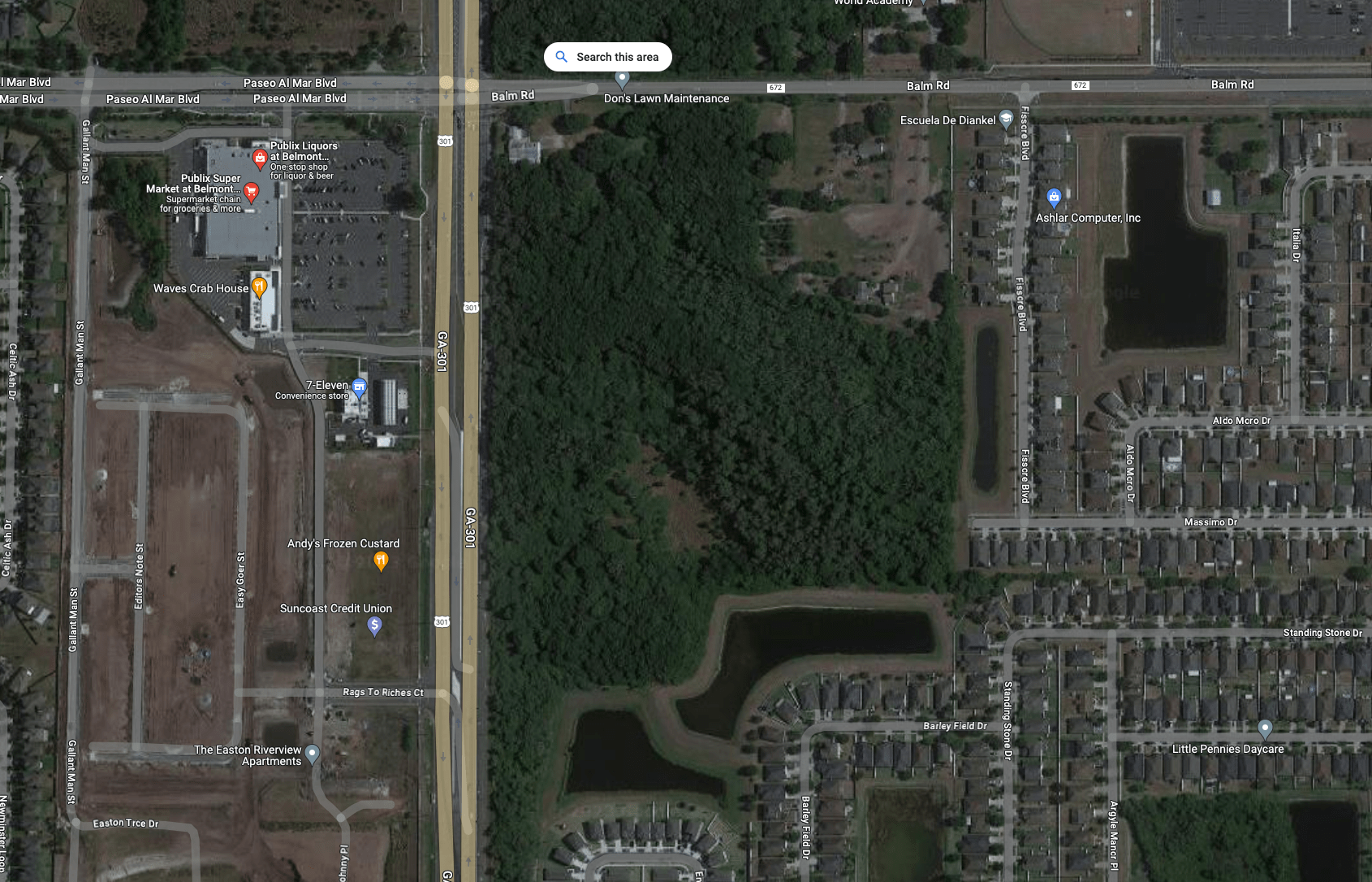
Google Maps
Bing Maps
ArcGIS
street view

Attack Paths
- Ingress/Egress Points
- Potential chokepoints (for badge cloning)
- Structure floor plan
- Trash receptacle placement?


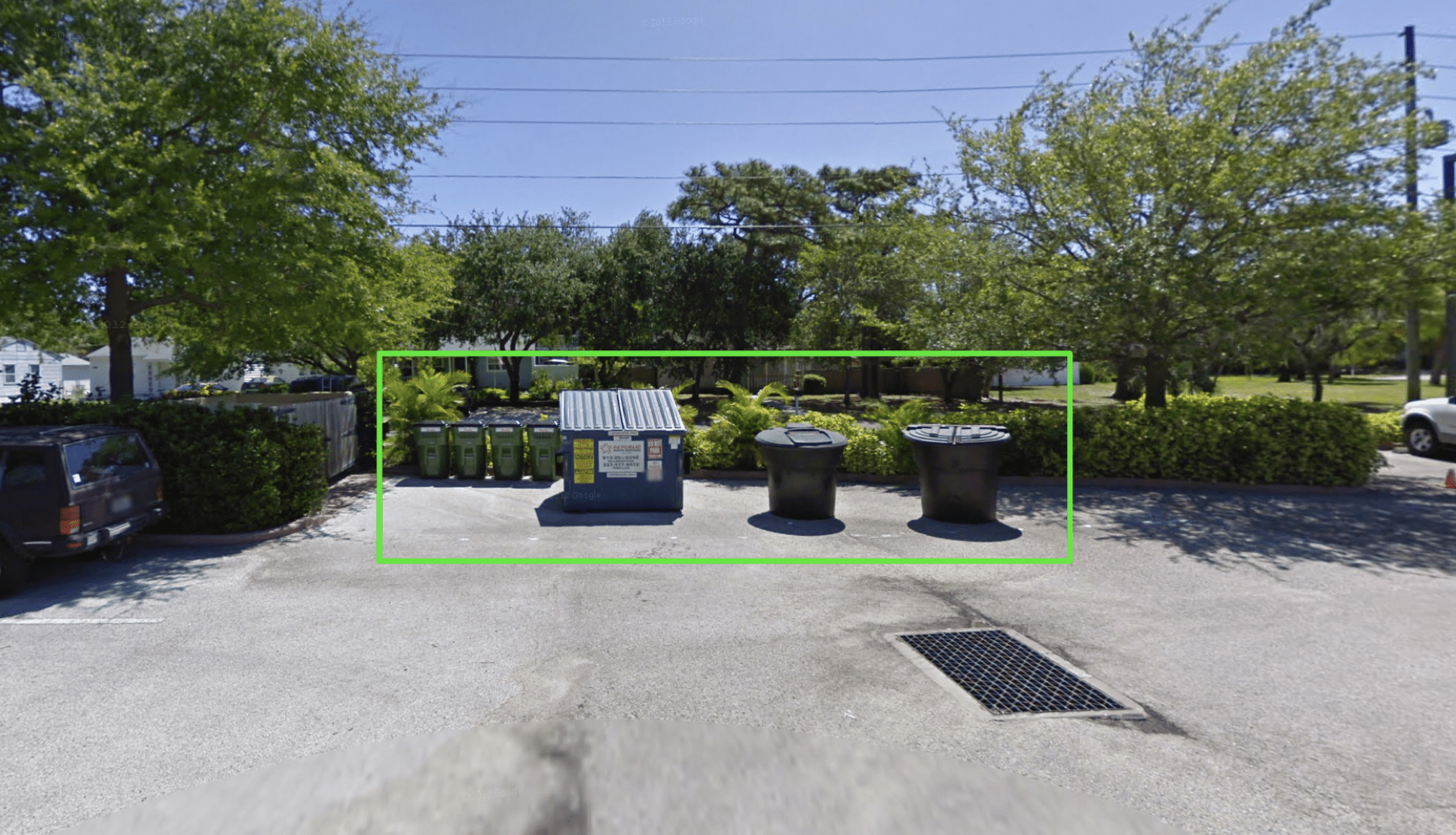
SURVEILLANCE
Types of SURVEILLANCE
Camera
PHYSICAL ACCESS CONTROL (PACS)
human
signal

camera

Types
- PTZs
- Static
- Viral Focal / Optical Zoom
- License Plate / Speciality
Object Recognition / AI
- Vehicle
- Human
- Face
- People Counting
Monitoring / Posture
- Active
- Passive
- AI Detection
camera Tracking


camera Face

pacs

RFID SystemS
- Log Badge Entry
- Log Badge Exit (where applicable)
- Log Invalid Badge Reads (take action)
- Tie Badge Reads to Cameras
- Keep Audit Logs
human

- Roaming Guards
- Active Monitoring
- Suspicious Activity Reports (Employee)
SIGNAL

Bluetooth
- Track known bluetooth devices
- Some systems can tie this to employee
Wireless
- Track known BSSID
- Tie to company workstations
FACILITY HARDING
Types of harding
Camera
PAC's (PHYSICALITY Access control)
human
signal
POLICY

CaMERA

Harding
- Placement - Out of reach
- Outdoor rating
- Redundant systems
- power
- recording
- Backups

RFID

- Well lit area w/ 24x7 camera coverage
- Non-cloneable technology (Elite Keys)
- Card Control
- Outdoor rating
- Redundant power system
- Backups
- Multi-factor (e.g., Card & Pin Code)
- Biometrics
- Disable unused technology on multiClass readers
- Security screws w/epoxy
- OSDP

Doors

- Exterior doors should be well lit and have at least one camera
- Mechanical locks:
- should be high-security
- no air gaps around the frame
- protected by latch guards
- Interior doors (sensitive office space):
- Use ADA handles with a smooth fall-off / taper
- Camera coverage, lights, and/or over head mirrors
- Minimal air-gap / latch guard if applicable
- Anti-piggybacking sensors on employee only / sensitive areas
- Badge access required for each floor
GUARDS

- Consistent staffing: Make best efforts to retain proven/effective guard staff
- Quarterly Training & Assessments: Incident response war games
- Roaming Patrols: Should be at random not at specific times
- Reactive / Proactive Posture: Determine what can be logged and what requires immediate attention
- Video Monitoring & Access Control Monitoring: Recommend active monitor in cases where personal harm is of concern
- Guards should guard, they should not also serve as receptionists
Network

- Lock down ethernet ports
- Wireless encryption
- Wireless authentication
- Secure workstations
- Added security for servers
- Implement additional security measures
- Isolate security controls, PACS, and cameras
Policy

- Create a physical security policy
- Guard posturing & response
- Employee responsibilities
- Business risk acceptability
- Assess the policy
- Guard: Conduct readiness to assess incident response
- Employee: Conduct human focused security assessments (e.g., SE and tailgating)
- Business: Goal focused threat emulation assessment, annually at a minimum
- Create a list of risks / issues and prioritize remediation and investment
- Amend the policy
- Reassess to gauge effectiveness
DETECTION
getting alerts

cameras
- Offline
- Face Match
- After-hours Activity
- Trip wires
- License Plates
PACS
- Bad badge reads
- Unusual activity (Late hour access)
- Offline Badge Reader
- Imposable Badge Read
human
- Suspicious Activity Reports
response
response planning

- Create a physical security response plan
- What are you going to do
- Who are you going to notify
- How will you contain the incident
SHAMELESS PLUG...

Three Days / Tampa, FL
- Pre-sales & Authorization
- Remote Reconnaissance
- Digital Surveillance
- Surreptitious Entry Tactics
- Badge Cloning & Replication
- Post-Exploitation
- Live Facility Breach Exercise
Upcoming Dates (2024):
July 17 - 19
October 16 - 18
PRIVATE TRAINING AVAILABLE
Tooling Available
Tooling Available
RAFFLE

PRIZE
- 1 x seat in a future Practical Physical Exploitation Course (travel and expenses not included)
- 1 x Under the Door Tool from the PhysicalExploit.com store
- 1 x PPE REX Sensor Bypass Gun
Your Mission
To earn your raffle ticket for the Practical Physical Exploitation giveaway, you must recover Thomas L33t's access code and enter it in the ticket staging box at the Black Hills Information Security booth before 6 PM on April 12, 2024. However, if you enter the access code wrong three times, the doors lock forever.
Questions


How to Secure Your Facility
By mwgroup
How to Secure Your Facility
Venture into the mindset of an adversary to fortify your facility against physical breaches. This presentation distills essential strategies from the in-depth Practical Physical Exploitation course, tailored to those responsible for safeguarding assets. Participants will uncover the difficulties of securing a site through the lens of red team professionals. Delve into the art of employing defensive controls, conducting Thorough Reconnaissance for weak points, deploying Surveillance to deter and detect threats, profiling potential threats effectively, and reinforcing Access Control to resist unauthorized entry. This session provides an arsenal of proactive measures and a critical evaluation of common vulnerabilities, arming you with the knowledge to transform your facility into a high security facility.
- 255




